Archive for the 'Software' category
Tandy Deskmate
September 17, 2007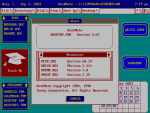 I first experienced this desktop software while using a Tandy 1000 RL machine which my father decided to go out and buy at the last minute on Christmas Eve, so I wouldn’t be disappointed. It was a nifty little machine with a 20 MB hard drive, built-in audio, 3 1/2-inch drive, and virtually no expansion capabilities what-so-ever. It had one ISA bus; everything else was pretty much hardwired into the system. It did have serial and parallel ports which allowed you to plug-in a MODEM or printer which certainly helped later on. After booting it up, I discovered the manufacturer had installed DeskMate onto a read-only partition on the harddrive. Much to my dismay, they had pre-configured it at the factory. When I needed to reinstall the system sometime later, DeskMate never functioned like it did out of the box. For some reason, and I have yet to figure out, it was about two or three times slower.
I first experienced this desktop software while using a Tandy 1000 RL machine which my father decided to go out and buy at the last minute on Christmas Eve, so I wouldn’t be disappointed. It was a nifty little machine with a 20 MB hard drive, built-in audio, 3 1/2-inch drive, and virtually no expansion capabilities what-so-ever. It had one ISA bus; everything else was pretty much hardwired into the system. It did have serial and parallel ports which allowed you to plug-in a MODEM or printer which certainly helped later on. After booting it up, I discovered the manufacturer had installed DeskMate onto a read-only partition on the harddrive. Much to my dismay, they had pre-configured it at the factory. When I needed to reinstall the system sometime later, DeskMate never functioned like it did out of the box. For some reason, and I have yet to figure out, it was about two or three times slower.
When compared against other Windowing environments at the time, such as Windows 2.X or even Windows 3.X, it could hold its own. The major feature missing was network support, but even Microsoft products didn’t support that until Windows 3.11.Until DeskMate walked into my life, I had never experienced a visual desktop before. It was an exciting experience and I wanted to explore every nook and cranny. First and foremost, I wanted to write software for it, so I phoned the number provided by Tandy Corporation in our manual. They said I needed to purchase the software development kit (SDK) and a suitable compiler. At the time, I didn’t know what a compiler was so I thanked the person and went about calling local stores and asking them questions. After a bit of research I discovered that the SDK was expensive and so was the compiler, which according to the sales person was a “program to make other programs.” They were probably brushing me off since I was basically a kid (or a young punk) at the time. I know they were at least a few hundred dollars a piece which put them out of my price range. In the end, I’m happy I didn’t invest the money in the SDK since I have since learned it wasn’t very good. Apparently, many companies had to write much of their own code in order to do anything useful. I would still like to check out the API, so until then, I reserve final judgement.
DeskMate had all sorts of small applications available. It had all of the standard applications like a word processor, simple database, spreadsheet, drawing application, telecommunications software, etc. These applications are extremely simplistic compared to what is available today; although the word processor did have spell checking and even a thesaurus and dictionary (purchased separately), and the database was functional enough to be useful. It even installed a personal diary program, which was very well done. It also came with a variety of useful on-screen tutorials to help you learn the software as you use it. Microsoft Windows didn’t have anything that helpful until Windows 95.
Categories: Reflections, Retro, Software
1 Comment »
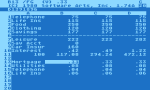 I was exposed to this piece of software at about the same time I was learning how to send graphical data to our printer. I didn’t really appreciate the complexity of this software until much later. My father was the one who was the real expert, but I also fired it up to help with my homework and to calculate some values I needed for a few of the games I was writing. It was the first time I had ever seen a spread sheet program, even though it appeared on the Apple II a couple of years earlier. Financially, the program was a boon for Apple and almost single-handedly lead to the mass adoption of the system. Financially, I’m not sure how it fared on the Atari since it took the company about a year to port it to other systems, but it’s common to see systems for sale on eBay which are being sold with a few games, miscellaneous pieces of software, and VisiCALC.This spread sheet software introduced me to a world where software can be used for something other than playing games. Although, let’s face it, they’re not as much fun or practical these days. I think I absorbed that idea pretty well for a boy who hadn’t quite entered his teenage years. I started to think about how I could write programs for my father which would help him with his financial chores. I don’t think I produced anything terribly useful, but I did write a few small calculator programs which could do a few interesting calculations involving trigonometry and simple algebra. I hadn’t yet discovered decimal encoding techniques like Binary Coded Decimal (BCD), but I eventually learned that Atari used BCD routines in its library implementation which BASIC used extensively. VisiCALC was able to handle floating point values efficiently because it was written in assembly language and the 6502 processor has floating point instructions available. The programmers used these instructions directly instead of using Atari’s library, which had a very positive impact on performance.
I was exposed to this piece of software at about the same time I was learning how to send graphical data to our printer. I didn’t really appreciate the complexity of this software until much later. My father was the one who was the real expert, but I also fired it up to help with my homework and to calculate some values I needed for a few of the games I was writing. It was the first time I had ever seen a spread sheet program, even though it appeared on the Apple II a couple of years earlier. Financially, the program was a boon for Apple and almost single-handedly lead to the mass adoption of the system. Financially, I’m not sure how it fared on the Atari since it took the company about a year to port it to other systems, but it’s common to see systems for sale on eBay which are being sold with a few games, miscellaneous pieces of software, and VisiCALC.This spread sheet software introduced me to a world where software can be used for something other than playing games. Although, let’s face it, they’re not as much fun or practical these days. I think I absorbed that idea pretty well for a boy who hadn’t quite entered his teenage years. I started to think about how I could write programs for my father which would help him with his financial chores. I don’t think I produced anything terribly useful, but I did write a few small calculator programs which could do a few interesting calculations involving trigonometry and simple algebra. I hadn’t yet discovered decimal encoding techniques like Binary Coded Decimal (BCD), but I eventually learned that Atari used BCD routines in its library implementation which BASIC used extensively. VisiCALC was able to handle floating point values efficiently because it was written in assembly language and the 6502 processor has floating point instructions available. The programmers used these instructions directly instead of using Atari’s library, which had a very positive impact on performance.
For more information on the development of VisiCALC, there are a couple of sources on the Internet available including one from the creators themselves.
Categories: Atari 8-bit, Reflections, Software
No Comments »
Atari 8-bit OS
September 10, 2007 Atari DOS – This operating system was the first operating system I was exposed to during my youth, and the 2.x series was the most popular in my household. The operating system was loaded off of 5 1/4″ double-sided double-density diskettes which usually offered about 320 KBs of storage space after formatting, although other disk formats offered less or more storage depending on density. The operating system did little more than manage disk functions such as formatting diskettes or erasing and copying files, hence the full name “Disk Operating System.” It could, however, be used to boot strap the cartridge or run a binary program at an arbitrary address after it was loaded. The DOS was mostly used to access files and programs stored on floppy diskette. It provided a File Management System (FMS) which needed to remain in memory in order to provide disk access functionality to other programs.
Atari DOS – This operating system was the first operating system I was exposed to during my youth, and the 2.x series was the most popular in my household. The operating system was loaded off of 5 1/4″ double-sided double-density diskettes which usually offered about 320 KBs of storage space after formatting, although other disk formats offered less or more storage depending on density. The operating system did little more than manage disk functions such as formatting diskettes or erasing and copying files, hence the full name “Disk Operating System.” It could, however, be used to boot strap the cartridge or run a binary program at an arbitrary address after it was loaded. The DOS was mostly used to access files and programs stored on floppy diskette. It provided a File Management System (FMS) which needed to remain in memory in order to provide disk access functionality to other programs.
Believe it or not, there are still hardware/software hobbyists and professionals creating products to use with your Atari. I have a software solution called A.P.E. which allows me to use my computer as a virtual disk drive, printer, modem, etc. It’s absolutely fantastic and accelerates software loading to a fraction of the time it took before. There are also products which allow you to connect a hard drive through the cartridge port, or even USB devices!
 A.P.E. stands for Atari Peripheral Emulator and is an essential piece of software for any Atari user. Until a few years ago, I was forced to play my Atari games via an emulator or on the Real McCoy using the terribly slow, but wonderfully nostalgic floppy disk drive. I don’t think it’s necessary to mention how painful it was waiting for the disk operating system to load, and then waiting for the actual game to load, and then waiting for the game to save, and then waiting for the game to load the second disk… you get the idea. There was a lot of waiting, and somehow I mangaged to do it without batting an eye lash in 1984.
A.P.E. stands for Atari Peripheral Emulator and is an essential piece of software for any Atari user. Until a few years ago, I was forced to play my Atari games via an emulator or on the Real McCoy using the terribly slow, but wonderfully nostalgic floppy disk drive. I don’t think it’s necessary to mention how painful it was waiting for the disk operating system to load, and then waiting for the actual game to load, and then waiting for the game to save, and then waiting for the game to load the second disk… you get the idea. There was a lot of waiting, and somehow I mangaged to do it without batting an eye lash in 1984.
First and foremost, A.P.E.’s biggest strength comes in the form of its disk drive emulation software. In order to get it to work, you must own a working Atari computer. The author probably explains exactly which Atari computers are compatible somewhere on his website, but I can tell you for sure that the Atari 800 XL and Atari 400 computers work like a charm. Simply connect your Atari computer to your personal computer using a custom SIO interface cable. The cable can be purchased through the web site, or you can even make your own if you’re so inclined. Install the APE software on a computer, configure it, select a disk image, and boot up your Atari machine. Voila! The software you selected will boot in record time. Plus, your personal computer now acts as a virtual hard drive for your Atari! You can put away those floppy diskettes, all of your games and applications can be saved and archived as an “ATR” file, which A.P.E. can understand.
Categories: Atari 8-bit, Reflections, Retro, Software
No Comments »
Microsoft LAN Manager
July 25, 2007After I had finished assembling my RetroBox, I was forced to to make a decision on what operating system to use. I chose to go with Windows 98 because I needed to be able to access my network. I also wanted to be able to boot into a DOS shell, but I didn’t want to dual-boot the machine. By writing a few options into the CONFIG.SYS and AUTOEXEC.BAT files, the user is presented with a small set of choices which may drop them into the shell. When I need to access files on my network or if I want to print something, I choose an option which boots me into Windows. My RetroBox is not a terribly fast beast, and it takes a while to boot and log-in.
To help alleviate this problem, I installed Microsoft LAN Manager in my DOS environment. Now I can access my network files and print through the network with ease. The process was a little frustrating and your experience may vary. I am providing this information, just in case you’re considering tossing the whole project and moving to Tibet to become a monk (if you’re already a monk living in Tibet, then you may be considering moving to Canada to become a Mountie).
The very first step would be to obtain a network card. For compatibility reasons, a popular 10/100 Mb card would be optimal. I have compiled a list of network card drivers which are bundled with Microsoft LAN Manager (which I will now be calling LAN Man to save some typing). Even if your network card is not on the list (mine wasn’t), you may still be able to obtain a driver from the company’s web site. My card is a D-Link “DFE-538TX Rev. D” and the earliest driver posted on the website was for Windows 98. After decompressing the file, however, I found a driver specifically for LAN Man which saved me from having to create a custom NIF file. I will explain how LAN Man uses these files a little later.
Once the physical card is installed, unpack your installation and run SETUP.EXE to get started. For many people, the setup process should be pain-free. My setup was not so problem free, however. I suppose it was due to the fact that I was running the Windows 98 shell, and not a pure MS-DOS, PC-DOS, or FreeDOS installation. I believe the root of the problem stemmed from the fact that the Windows 98 shell doesn’t like the ‘$’ wildcard. If you take a look at the SETUP.INF file, you’ll notice a number of files ending in the dollar sign. Within the file, a program like NetBEUI would be referenced like this:
DRIVERS\PROTOCOL\NETBEUI\NETBEUI.ex$
Under MS-DOS, this would match the file NETBEUI.EX_. Under the Windows 98 shell, it does not seem to match it at all, so the installer complains that it cannot find the file. What I did to correct this problem was to simply change the wildcard to the ‘_’ character and presto! The installer was able to see the file and continue with the installation.
Because my card was not on the list of available drivers, I needed to add it to the list myself, which meant making an entry in the SETUP.INF file so it could find the driver files (<DRIVER NAME>.DOS and PROTOCOL.INI) and the Network Information File (NIF). After making an additional entry in the SETUP.INF file and copying the files to the right locations (under DRIVERS\ETHERNET), the setup program correctly enumerated the card name and I was able to select it from the installation menu.
After these changes, the install carried on happily, but complained at the very end that it could not find the “NETWKSTA.” file. There is no “NETWKSTA” file; it’s just a directory. This is the eight-character directory shorthand for Network Work Station. I don’t know why it was complaining, but it’s an important program and needs to be installed so you can use network resources like shared files and printers. This is also easily corrected after completing the installation. Just copy the file:
\MSLANMAN.DOS\NETWKSTA\NETWKSTA.500 to
\MSLANMAN.DOS\NETPROG\NETWKSTA.EXE.
Don’t copy it from the CD-ROM, because that file is compressed and won’t run. That file will end in an underscore, so it won’t match the name I listed above.
During the network setup portion of the installer, if you choose to use DHCP then you don’t need to specify an IP address or sub-net mask. For log-in credentials, just supply a user name without a password if you don’t have an MS LAN Manager or Windows NT authentication service setup. When it asks you for a domain name and you don’t know what that means, just enter in a dummy name or leave it blank (I didn’t try leaving it blank, the installer may refuse to continue). One item to keep in mind: a Windows domain is not the same thing as a work-group, but I used my work-group name anyway since I knew it wouldn’t matter. Eventually, if I choose to setup a domain, I will change the domain name at that time.
After moving the commands inserted into my CONFIG.SYS and AUTOEXEC.BAT files around to suit my own taste, I rebooted the machine and ran the NET.EXE program. Using this software, I could enter the UNC path to one of my machines:
\\MACHINE1
Go to the view menu and select “View available network resources”. It will present you with a dialog which will allow you to assign a shared folder to a local resource like a drive letter. I was able to read and write (provided the permissions are set appropriately on the share) to the folder using the new drive letter (F: in this case).
Please note: you won’t be able to mount a printer or a shared folder if the share name is greater than eight characters! It will simply complain that it cannot find the network resource.
Categories: DOS, Software
No Comments »
Exult v1.2 API Documentation
July 10, 2007Since I couldn’t find any on their site, I’ve churned through the Exult engine using Doxygen to produce a usable set of API documentation. It’s a good reference to get a handle on their overall architecture in case you felt like diving a little more deeply.
Categories: Programming, Retro, Software
No Comments »
Introducing CircleMUD
July 7, 2007During the early 1990s, the Internet was fairly new to most people. At the University I attended for a time, we were using a PC-DOS based environment which had Novell’s Netware stitched on top of it. At the time, I had a small number of Usenet news groups I liked to read every morning, and I stumbled across a post by an individual in alt.rec.gaming or the like. This was before the days of spam and prolific pornography, so when a person posted a message with a subject line like “Check out this cool site!” You had no reservations whatsoever about following the link.
The link he provided wasn’t a URL which could be viewed in a web browser, but looked something like this:
telnet://chaosrealm.darkmatter.org:4000/
Until I started paying to go to school, the only experience I had with a public network in the late 1980s was through local Bulletin Board Systems. I could e-mail people on other BBS systems through something called FidoNet. Those systems would use a BBS mailer for the users to create their message (or it could be uploaded using a pre-formatted text file), and then copy it over to the FidoNet servers for transmission using specialized protocols. The mailing address was rather complicated and needed to have a series of names, symbols, and numbers affixed to it if you ever expected it to reach its destination. Due to my own inquisitive nature and two very understanding parents, I was able to set up and experiment with computer communication. As a result, I was somewhat more experienced with networking before entering University than your typical freshman, but I had never used a telnet client before. It was certainly a mystery that needed solving. Little did I know what worlds waited for me on the other side. Nowadays, there is a bare-bones telnet client on virtually every desktop. Under the Xandros operating system, the program is called “telnet.” Likewise for Microsoft Windows and MacOS X.
After a bit of research, I discovered what I needed to access the site, so I started poking at the client program. A friend of mine saw what I was doing and thought it looked interesting, so he pulled up a chair and logged into his own terminal. What we saw was disappointing at first. It was essentially a blank screen with a small title surrounded by credits centered in the middle and a login prompt near the bottom left-hand corner. I knew neither of us had an account, so I thought our little adventure would probably end right then and there with a message like “Invalid login” or “Permission denied.” Instead, we received a prompt asking “Are you sure you want to use this name?” Tentatively, I declined and sat staring at the screen for a few seconds. I was familiar with the concept of a “handle” or nickname from the BBS systems I frequented. I remember not wanting to use the name I had entered, which was probably something unoriginal like my first name. I don’t remember the name I chose and it’s probably for the best. Little did I know, the interesting questions would soon follow.
The server accepted my new name and prompted me for a password. It then asked if I wanted to be “[M]ale, or [F]emale?” During my role-playing sessions, I had never considered being a woman, even though friends of mine tended to flip-flop between the sexes just for fun from time to time. I guess it just wasn’t something I even thought about. My teenage philosophy was black and white: how could I be a fearless knight of the realm with breasts? However, faced with the same opportunity on my computer, I did pause for the briefest of moments. Anonymity is not somethings easily overlooked by most people. Not wanting to appear unmanly in front of a friend, I quickly pressed the ‘M’ key. To this day, I have never played as someone from the opposite side of the gender coin. I eventually realized it didn’t really have an appeal for me. If I was going to invest the time creating a character in this new world, I needed to take it seriously and not go galavanting around the realm trying to fool everyone into thinking this body is real and I know how to use it. Besides, I really don’t think I would be able to do a very good job of it. I would probably end up over-acting and annoy everyone in the game while fooling no one at the same time. And then there’s the whole psychological impact of sustaining an Internet female persona…
Depending on the site you visit, the questions don’t necessarily end after you choose your sex. There can be questions about your race, occupation (warrior, cleric, mage, or dentist), attributes, and a description for your character just to name a few. Before you start hammering away at the the keyboard, it’s important to realize these details will be visible to other people. The site I visited that day was classified as a MUD which stands for Multi-User Dungeon/Dimension. There are many other classifications of multi-user software environments such as MOOs, MUCKs and so on, but I have only been interested in dungeons. A MUD is a world tapered in such a way the user will feel like their transported into an interactive book. All of the details in a MUD are described by words; there are no sounds, graphics, or vibrating joysticks. The illusion is helped along by talented authors and other player characters. Just like actors and actresses, most people who enter a MUD want to remain in character while they’re on-line, so information about their personal lives are usually not revealed. If they want to elaborate on their real life, then they usually initiate a private chat or use special abbreviations to illustrate they are speaking out of character.
The software hosting the MUD is stateful. It knows when you’re logged in and when you’re not. When you’re naughty and when you’re nice. By your command or when you log off, it can record vital details about your character like the equipment you’re carrying, the money you’ve accumulated, and other pertinent details. Anyone familiar with games like Dungeons & Dragons will feel right at home in this universe. In fact, it’s often a fun alternative to playing face-to-face, especially when you’re role-playing amigos live far away. Muds essentially run by themselves, but they can also be directed in real-time by controlling characters often called wizards, gods, or heroes. These characters have permissions to modify the world and initiate quests. Ordinary players can sometimes attain these positions by achieving a very high-level character ranking and then be offered a promotion, or simply participating in its day-to-day operations by becoming more involved. Sometimes it’s just easier to befriend one of the wizards and beg for an opportunity to prove yourself worthy. Just try not to cry if they refuse.
Wizards are usually programmers who typically interact with the MUD on a technical level. They usually have a character which is used to logon to the server in order to test the deployment of a new feature. It’s inadvisable to anger these people because they can eject you from the MUDvery easily. Their characters on the MUD are not ordinary players; they usually cannot be killed and they often make themselves invisible to ordinary mortals. This is a kind of power one can abuse. Do what you like on your own server, but I can guarantee no one will want to visit your realm if you abuse your abilities as a Wizard.
Back in the heyday’s of MUDding, there were literally thousands of these servers up and running on the Internet. And as a player, you had your pick of the litter. Low and behold, though, the majority of those servers were rehashes of existing worlds. There were a few bright stars amoung them, but it was a challenge to find a truly original MUD with a decent up-time. If you’re going to spend the time to create and manage a MUD, then I suggest you think of an original theme first and then come up with an interesting environment. It could be used as an interesting spot where you and your friends and family can hang out instead of the typical chat room.
Interaction on the MUD is accomplished via text commands you feed to the server hosting the game. These commands and transferred over the Internet via the telnet protocol and then the response is sent back to your client in a timely manner. So, what commands are available for you to use? It depends on the server software, but they are very similar to the commands used by many classic adventure games. At some point in their history, games like Leisure Suit Larry and King’s Quest all sported a command interface where you typed what you wanted the character to do. For example, commands like “take bottle” or “look at painting” were commonplace. MUD commands were pretty much the same, except they could usually handle more complex sentences and contained a larger set of available commands. There is also the multi-player aspect to consider. A MUD needs a much more extensive set of commands used for communication like “shout,” “talk,” “whisper,” or “emote.” These all have different effects based on your permissions and proximity to other players. For example, some MUDs do not allow just anyone to shout a message, since it will usually be heard by everyone currently logged into the MUD. Players in the past have used this feature to be very naughty.
Due to its popularity, you would expect there to be a lot of MUD software available on the Internet and you would be right in thinking so. From this point onward, we’ll be studying an implementation called CircleMUD. CircleMUD was created by a man named Jeremy Elson in 1993 and is a worthy extension to the DikuMUD codebase which was written by Katja Nyboe, Tom Madsen, Hans Henrik Staerfeldt, Michael Seifert and Sebastian Hammer in 1990. It is stable, well programmed and documented and certainly one of the more popular servers available today.
Before we delve too deeply and greedily, I think it’s worth talking about the software license. You can use the software free of charge, but you must comply with the license agreement, which basically has three requirements. First, you can’t make any money off of CircleMUD. That also includes soliciting funds or accepting donations. Second, you must give the authors credit for their hard work. And lastly, you must comply with DikuMUD license. All of these details can be found in the documents accompanying the distribution.
Categories: Retro, Software
No Comments »
VMWare for Games?
June 29, 2007 ![]() Just for kicks, I decided to try and install FreeDOS into the free version of VMWare server yesterday. The installation went very nicely and before long I was mucking around in the console. I decided to try and play a game in this environment. Having used FreeDOS before, I knew it would work with the operating system, but I was unsure how playable it would be under VMWare.
Just for kicks, I decided to try and install FreeDOS into the free version of VMWare server yesterday. The installation went very nicely and before long I was mucking around in the console. I decided to try and play a game in this environment. Having used FreeDOS before, I knew it would work with the operating system, but I was unsure how playable it would be under VMWare.
The first game I tried was Blake Stone: Aliens of Gold and it ran quite well. I was encouraged so I decided to try a more complex game. I chose DOSDoom because I love the game and it seemed like the next logical step. It also ran well. To try out your own game, just run an ISO generation tool on the installed directory, and attach the ISO to your VMWare guest. If you’re running Xandros, use the ‘mkisofs’ command:
$ mkisofs -o /tmp/doom/cd.iso /tmp/doom/DOOM/
Assuming your installation directory is located under ‘/tmp/doom/DOOM’, this command will quickly generate an ISO file. To make it easier on yourself, I would just throw all of your favourite games into one ISO, burn the CD, archive it (you can edit it later if you want to add more games), and use that whenever you feel an itch to play.
This technology is a fabulously free alternative to building your own RetroBox, but maybe not as much fun to put together.
Categories: Games, Retro, Software
No Comments »
Simulation or Emulation?
April 19, 2007When people in the gaming community speak of emulation, they are usually referring to the emulation of a hardware console or a computer system. This software allows them to play games on hardware systems which were never engineered to allow it. Imagine, playing Super Mario Kart with your friends through the Internet on your Mac OS X, Xandros, or Microsoft Windows computer. Impossible? Google the ZSNES or SNES9X project for more details.
First of all, there seems to be some confusion over the use of the terms “emulation” and “simulation” on the Internet. It seems many people (myself included) are referring to programs, such as DOSBox or ZSNES, as emulators. Usually, I abhor ignorance (unless it applies to me somehow), but thankfully it’s not simply a misused term stemming from the ignorant, adolescent population on the Internet.
Part of the confusion may come from people in the hardware industry referring to simulators as software that precisely mimics hardware, and emulators as pieces of hardware that are precisely controlled by software. Reread that last sentence since there is a distinct difference in their meaning. For people in the software industry, the terms are a little different. When a programmer attempts to duplicate hardware components through software, it’s often referred to as emulation. Simulation, on the other hand, can be used to mimic the actions of a piece of hardware or software, but the internal workings may be completely different than the original product. It may look and act like an Atari computer, but it’s not really using any of the core components of that machine. Within the realm of software, simulators can also apply to programs which simulate completely different systems such as organic or chemical interactions, economic or disaster forecasts, or the weather.
I’m going to digress for a moment and talk about a simulation used to provoke this global warming hysteria we all are experiencing today. Simulations can be as simple as simulating the periodic movement of a pendulum, or as complex as a weather system. Simulations can also involve complex interactions between other systems, and for these intricate systems to be effective at predicting or postulating outcomes, they must rely entirely on our flawless understanding of how all of these systems work. It’s funny (and sad) to read about simulators which can accurately predict the effect of human pollution on the weather system. These are probably two of the most complex environmental systems attempting to be simulated today. It’s no surprise that even the most sophisticated simulation models used today don’t work, but various environmental groups and political leaders are running with the “evidence” as if it were iron clad proof. The only way they got the simulation to output the desired result was to modify the data going into the system. Now, I’m sure we’re not all scientists here but it should be fairly obvious that manipulating data to validate your own hypothesis isn’t exactly following the scientific method. I don’t want to get off on a tangent here, it’s a good example of simulators being used today and the unexpected complexities that can arise during the development of a simulator.
Most of the time, programmer’s would not attempt to simulate an entire machine, but rather couple the simulation with emulated components. The reason is simple: it’s a lot more work to simulate an entire machine than it is to emulate one. In a simulation, none of the original software for the hardware platform can be used, which means it too must be simulated. Looking at the other side of the coin, we see that pure hardware emulation is also not very practical to implement through software. How does one emulate a hardware bus, for example? The bus is purely an electrical component and has little to do with the purpose of the overall system. Yes, hardware engineers need to implement bus systems, but programmers attempting to emulate the machine can forget about it entirely. Simulation is often used in place of arcane hardware constructs which are part of the electrical system or those pieces which simply cannot be emulated. It acts like a bridge between discrete or unrelated pieces within an emulator so that the emulator can function as a cooperative unit.
When writing an emulator for a video game console, it’s vital to get as much information about the hardware as possible. Doing so will hopefully give you the big picture, and make it easier for you to divide your work into component groups. In a simple system containing only one central processing unit, for example, you will need to emulate the operation of the chip. This includes instruction sets, registers, any available memory caches, and operands, which constitute the general make up for most microprocessors. Advanced microprocessors necessitate advanced emulation, but not all components of a microprocessor need to be emulated in order to maintain accuracy. For example, optimization features used by the chip can essentially be omitted for a perfectly functioning system, unless those pieces modify the data in a peculiar way or they contain a bug which affects the software’s presentation or operation on the original hardware.
Another component group needing particular attention would be the memory subsystem used by the console. The memory architecture used could be as simple as a linear array of addresses or as non-intuitive as paged memory or memory-mapped input/output. The solution chosen for emulating memory should probably favor reading memory over writing memory, since the former occurs a lot more frequently. Some systems, such as the Nintendo Entertainment System, allowed the clever engineers to essentially extend the available memory through the cartridge. They used bank switching within the cartridge to overcome the addressing issue normally encountered when a system attempts to extend the range of available memory than what was originally available.
I could go on and on as there are many other aspects to consider before writing an emulator, such as debugging or functions related to emulation as an application but they are outside the scope of this little write-up.
Categories: Software
No Comments »